Security is a weighty concern in a world where IoT is becoming significantly more prevalent, and developers are constantly looking for effective security solutions to address this matter. Hardware-based systems typically offer more complete protection for IoT systems as opposed to software-based systems, and as such, Microchip has developed a robust security mechanism in the form of cost-effective, low-power security co-processors. Learn more about these solutions (which are compatible with any MPU or MCU and allow you to quickly implement security into your embedded systems) and discover the potential of hardware-based key storage for IoT applications with Microchip’s line of efficient and effective security co-processors.
Securing the Internet of Things (IoT) is a hot topic right now, especially as new instances of security breaches come to light. Stories of hackers taking control of a vehicle that was cruising on the highway at 70 miles per hour, of a flying plane being hacked via its in-flight entertainment system, and of smart meters in Spain being compromised for energy theft have helped to make IoT security a huge concern for consumers as well as embedded designers. The value and benefit of smart, connected devices has been overshadowed by uncertainty about the security issues that may come with them.
Security requirements for the IoT are radically different from those of traditional embedded designs because small, intelligent IoT nodes must be able to authenticate themselves to the ecosystem with limited or no human interaction. In order to do this, their cryptographic credentials must be stored in the device itself. Since edge nodes are often physically accessible, these credentials are in danger of exposure to hackers.
There are three major pillars for securing IoT designs: authentication, encryption, and security key storage. While authentication and encryption are equally important building blocks in the security equation, it's important to recognize that encryption doesn't ensure security in IoT applications. Since it is generally too daunting and time consuming to hack into complex authentication and encryption systems, the majority of hacks are usually implemented by using imposter devices to break into the areas where secret keys are stored. The loss of these security keys severely impacts the authentication and encryption processes. In other words, once hackers get hold of the keys, the other two protection mechanisms can also be compromised or breached. Therefore, an IoT system is really only as strong as the process that is used for the storage of secret keys.
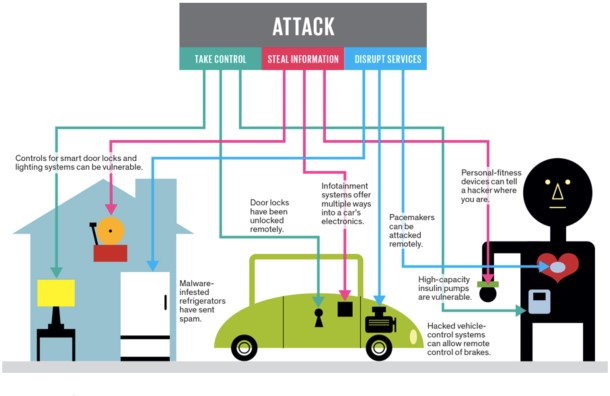
Figure 1. The diversity of the IoT world demands a new security paradigm.
To address this challenge, embedded design engineers have two options for implementing security in their IoT projects: software-based and hardware-based solutions. While software-based solutions have the advantage of flexibility, they generally don’t meet the needs of IoT systems. Hackers and spoofers can exploit software bugs to break into a network of devices. Updating the software with patches is a stopgap measure that sometimes only offers a temporary solution. On the other hand, hardware-based systems are far more difficult to spoof or hack than software-based systems, making them a more complete security solution.
IoT's Hardware Security Blueprint
In IoT designs, the authentication and cryptography security elements need to be implemented fairly early in the development cycle. Therefore, it is critical that IoT developers have a clear understanding of an end-to-end ecosystem for creating a robust security roadmap. The traditional approach to hardware security involves building the security stack on top of a microprocessor (MPU) or microcontroller (MCU). However, a significant amount of computing power is required to carry out security operations. For instance, precious CPU cycles are required to accelerate the authentication of applications and firmware. As a result, hardware solutions built around a central MPU or MCU have seen limited success because this compute-intensive authentication burdens the overall system and eventually slows down the device performance. Also, security solutions built on top of processors generally store the secret keys into memory, which can be accessed by clever hackers via intrusion mechanisms like snooping. Security co-processors or crypto elements can help resolve this design conundrum.
Enter Security Co-processors
A security co-processor is a separate chip that offloads security tasks from the main microprocessor or microcontroller while making authentication faster and less taxing on the overall product design. Its crypto elements offer protection against a wide array of security threats including IP theft, cloning, over-building, reverse engineering and infecting IoT devices with rogue code.
An IoT node or gateway is the central nervous system that handles a horde of sensors and other “things” at one end and resource-sensitive cloud computing at the other end. It can only be truly secure when the secret keys are stored in protected hardware. Using security co-processors in a node or gateway design will safeguard private keys, certificates and other sensitive security data to ensure authentication and protection against software, hardware and back-door attacks.

Figure 2. A crypto element allows small, low-cost IoT nodes to implement strong cryptographic security.
A security co-processor is a cost-effective addition and its crypto elements consume very low power, which is essential in IoT designs. Some other reasons to consider using security co-processors include:
- • They are equipped with hardware cryptographic acceleration to carry out strong authentication while they offload cryptographic code and math from the central processor of an IoT node
• They simplify the manufacturing process by effectively dealing with the key provisioning, a process of loading security keys and other security features like certificates onto a product
• They are pre-loaded with unique keys and certificates to ensure that encryption keys are secure throughout the manufacturing process, which also reduces complexities in manufacturer supply chains
• They replace the traditional approach of using the Hardware Security Module (HSM), which uses a database approach to store, protect and manage keys, as well as requires a significant investment in infrastructure and logistics
• They can also replace Trusted Platform Module (TPM) chips, which have their roots in the computer industry and are not well-positioned for low-price IoT edge applications; instead security co-processors facilitate certified ID platforms and can be deployed in IoT node-to-cloud environments, even at smaller scales.
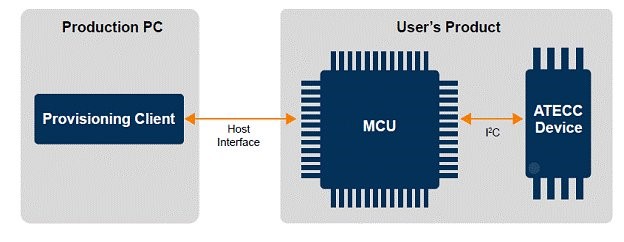
Figure 3. A security co-processor or crypto element offloads the authentication tasks from the main MCU.
A Complete IoT Security Platform
Since the IoT security paradigm is somewhat of a moving target—with multiple device types communicating with each other over a multitude of wired and wireless interfaces—IoT developers are relying on the expertise of chip suppliers that have years of experience in crypto hardware and security standards like TPM and Secure Hash Algorithm (SHA). Microchip not only offers a range of security co-processors that are compatible with any MPU or MCU, but also powerful development tools to help you implement security co-processors more quickly into your embedded systems.
Primarily targeting cost-sensitive embedded applications, the ATSHA204A crypto element is based on SHA-based symmetric authentication and uses 4.5K bytes EEPROM. The ATAES132A crypto element, based on the Advanced Encryption Standard (AES), boasts 32K bytes of secure serial EEPROM to facilitate faster symmetric authentication.
The ATECC508A crypto engine uses Elliptic Curve Cryptography (ECC) to create secure, hardware-based key storage for IoT applications that include home automation, industrial networking and medical. It employs protected key storage as well as hardware acceleration of ECC cipher suites, including mutual authentication with Elliptic Curve Digital Signature Algorithm (ECDSA) and key agreement with Elliptic Curve Diffie-Hellman (ECDH) techniques. It also ensures secure storage by utilizing the Hardware-TLS (HW-TLS) platform. The ATECC508A supports the CryptoAuth Xplained Pro evaluation and development kit and works with the CryptoAuthLib software support library. Proving that hardware-based security solutions do not need to be costly, the ATECC508A minimizes IT labor costs and licensing fees and is offered at very attractive prices for high-volume IoT applications.
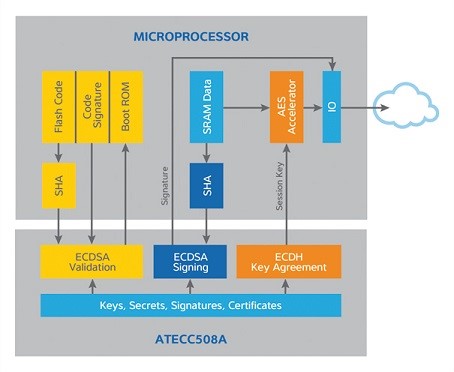
Figure 4. The ATECC508A crypto element first generates its own key and then carries out ECC operation to authenticate IoT nodes.
If you need world-class and cost-effective embedded security solutions for your IoT system design, visit the Atmel Security ICs web page to learn more about how our hardware-based security devices can reduce your costs and ensure trust for every system design.

