Introduction
With the awareness and concern over attacks and information theft, it is now a necessity to include rigorous security technology in all Internet-of-Things (IoT) and edge devices. This includes IoT sensors, controllers, and actuators, as well as edge computing, audio-visual security devices, and otherwise internet/remotely connected electronics. Part of this need is derived from potential security concerns with server and router hardware, which has recently been subjected to highly sophisticated malware, attacks, and information stealing exploits. And with reported increases of security breaches related to IoT devices in recent years, it is likely that IoT and edge device security is only going to be under increasing threat in years to come. [1,2]
Hence, there is a necessity to for security in every connected and networked device to protect the growing smart home, smart office, and smart city infrastructure. Until recently, the requirements for additional security required customized hardware solutions of devices to hold and encrypt/decrypt keys, as software security alone is inadequate for ensuring secure storage and authentication. The early challenges associated with conceiving, designing, prototyping, and finally, implementing hardware security were generally daunting, and the hardware solutions were often specific to a particular communications technology. This led to lax security in smart home and edge devices, including automobiles, security cameras, smart locks, sensors, thermostats, and edge computing solutions.
Fortunately, there are now integrated solutions that operate as Trusted Platform Modules (TPMs) that are communications technology agnostic. Furthermore, these new TPMs can readily be fitted on to Rapid Development and Prototyping Boards, such as the 96Boards to ease development. Moreover, Infineon Technologies and Arrow have partnered to create Infineon security chip-powered TRESOR Mezzanine Boards, with help from FAE Technologies, compatible with 96boards (Arrow Thor96), which eliminates the need for custom security hardware and extensive developer resources, and reduces the time to market for IoT and edge electronics solutions.
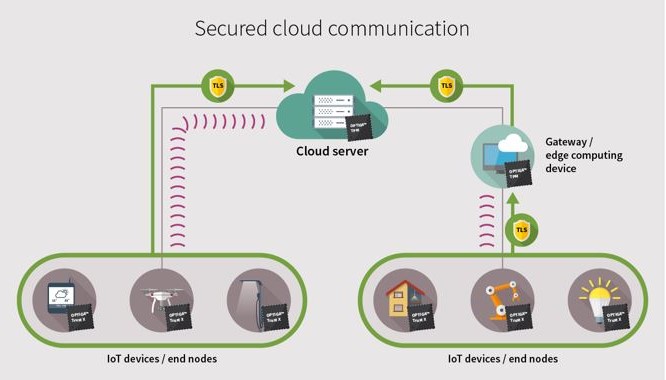
OPTIGA™ TPMs can be used to enhance the security of critical IoT and connected devices
Overview of Hardware-based Versus Software-based Security
Software-based security and encryption technologies have been in use since the first software was being developed. Moreover, the portability and interoperability of software-based encryption has led to its widespread use, from protecting entire platforms and organizations, devices and networks, to protecting data on portable storage devices. Software-based security and encryption is relatively easy to update and upgrade, and can be used to protect data being transmitted.
However, Software-based security is only as secure as the operating system running the software, and software-only security may not hold up to modern security demands [1,2,3,4]. As any operating system and software has bugs, attackers have become very good at exploiting these bugs as security weaknesses. Hence, any given software-based security and encryption method can be expected to have several unintended vulnerabilities from bugs and operating system weaknesses.
Moreover, software security technologies require additional processing, memory, and storage beyond the limited CPU and memory typically included in IoT and edge devices and may thus lead to the use of much larger and more power hungry processors and memory than would be necessary with hardware-based security technologies. Also, software-based security and encryption, unless also augmented with hardware-based secure storage, must rely on generally insecure memory and storage for vital security information, such as sensitive data and secure keys.
Good hardware-based security and encryption also doesn’t depend on the security of the host system, and is thus immune to operating system exploits and other software vulnerabilities. Additionally, many hardware-based security modules also contain their own secure storage, protected against software and operating system vulnerabilities. And the specialized cryptographic accelerators contained in hardware-based security modules avoids burdening IoT processor resources.
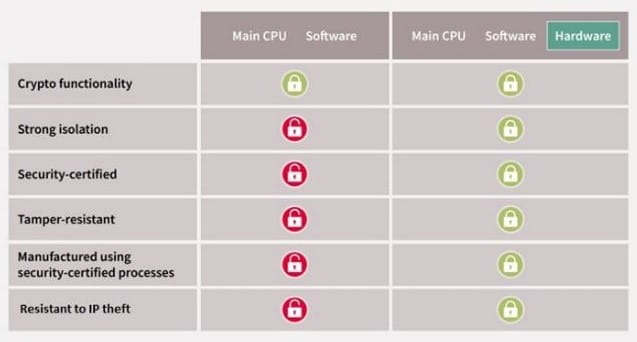
Security implemented in hardware combined with Software offers more benefits to IoT Device manufacturers than only security running on MCU
Benefits of Integrated Security Solutions
Some of the early arguments against hardware-based security and encryption centered on the additional cost, difficulty, and delay it would introduce into the production timeline. Custom hardware security solutions still face the same challenges. However, there are now readily available prebuilt security modules, such as a Trusted Platform Module (TPM), which offer standardized security, with modules that are designed to be compatible with even the most compact IoT devices or most rugged automotive and industrial devices.
TPMs provide several key hardware-based security features, namely digital device IDs, device authentication, secure communications, data confidentiality, IP protection, secure key storage, secure firmware updates, and support for a variety of encryption algorithms. TPMs efficiently generate, distribute, store, and manage cryptographic keys, including custom keys. If a TPM is manufactured in a certified secure production environment, then OEMs only need to integrate the TPM with the embedded device hardware without needing to redesign processes or modify the production environment. Moreover, the established TPM standard also supports secure over-the-air (OTA) updates, thus ensuring cryptographic agility over the life of the IoT or edge device.
As there is such an expansive diversity of IoT applications and use cases, a leading semiconductor manufacturer, Infineon, offers an incredibly wide range of standalone hardware-based security solutions: the OPTIGA™ product family [5,6]. This includes OPTIGA™ TPMs designed specifically for the standards and expectations of smart home, lighting, city, sensors, industrial, automation, gateways, routers, servers, and automobiles.
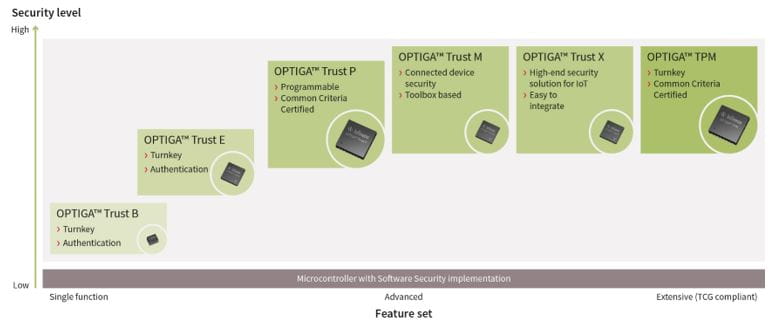
Infineon offers a wide range of hardware security solutions that are designed to offer superior security services for every type and level of IoT device
Highlights of 96Boards as a Development and Prototyping Tool
Development boards have become a necessary tool for prototyping and development of embedded systems. Initially, these development boards were only produced by and geared toward a specific processor with few I/O options. More recently, there have been industry initiatives to develop standardized development board platforms that can work with a variety of microprocessor units (MPUs) and incorporate an expanse of add-ons. 96boards are such an initiative, and now feature a huge variety of development boards fit for consumer, enterprise, and IoT applications [7].
96boards are a SoC-agnostic development platform compatible with ARM-based processors, and offer a cost effective and efficient way for hardware, software, and OS developers to work on common platforms that can be used for prototyping or even integrated into new systems.
A custom Arrow Electronics 96Board, referred to as the Thor96 Board, is a powerful quad-core single-board computer (SBC) with a dedicated GPU, dedicated VPU, Wi-Fi, HDMI output, Bluetooth, Thread/Zigbee, and myriad of I/O options [8]. These capabilities make this board an incredibly useful development tool for IoT and Edge-device applications, such as industrial PCs, servers, industrial controllers, or edge gateways.
Leveraging the TRESOR Mezzanine Board & Thor96 Board for Prototyping Secure IoT and Edge Electronics
Addressing the biggest challenges with prototyping and developing security technologies for IoT applications, a new mezzanine board compatible with 96Boards has been released that features two Infineon OPTIGA™ TPMs (SLB9670 & SLB9645) and an Infineon OPTIGA™ TRUST E authentication chip (SLS32AIA020A) [11]. This new TRESOR mezzanine board can be easily installed on a Thor96 Board, where Arrow-supplied example code can be employed to jump-start development and prototyping [9].
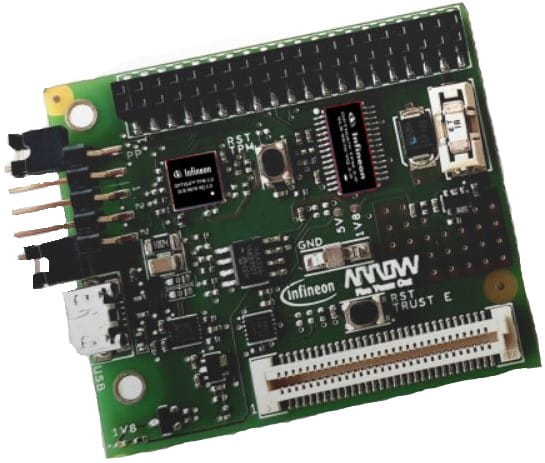
The TRESOR Mezzanine Board is an add-on to the popular 96Boards that includes secure TPM devices (OPTIGA™ TPM) from Infineon Technologies, as well as an authentication chip (OPTIGA™ Trust E)
With a TPM 2.0, TPM 1.2, and TRUST E authentication chip, hardware and software developers can explore a vast array of methods of implementing state-of-the-art security elements. The TRESOR board TPM 2.0 communicates over SPI using 96Boards standard LS expansion connector, while the TPM 1.2 chip communicates over I2C on the 96Boards standard low-speed expansion connector. The Trust-E authentication chip communicates using the same I2C bus as the TPM 1.2 chip. Furthermore, debugging is made much easier with an on-board UART to USB conversion chip, which enables debugging through standard USB to Micro USB interconnect. This mezzanine board is designed to be powered from the +5 V rail from the host board.
Connecting the TRESOR mezzanine board to the Thor96 board just requires plugging the mezzanine board into the appropriate slot, followed by a simple software setup. For the Application Note please visit the TRESOR board Product Page. A development PC with a Yocto built environment for the Thor96 board is the only other piece needed to begin developing secure elements with the Thor96 Board and TRESOR mezzanine solution.
How Thor96 and TRESOR Mezzanine Secure IoT & Edge Devices
One of the most significant vulnerabilities with IoT security is often the communications, either wired or wireless, between the IoT device and other IoT devices or edge devices. There have been cases where firmware updates, initialization processes, and assumed secure communications have been hijacked or intercepted by attackers and later used to install malware or gain access to other devices on the network.
The only way to prevent these types of attack vectors is to eliminate the insecure aspects of the communications exchanges. Built-in hardware security that ships with a device can encrypt and authenticate the communications from other network devices, as well as enable successful firmware updates and an appropriately response to anomalies. There may also be sensitive information stored on IoT and edge devices that can be exploited. Hence, TPM modules can be used to store sensitive information, along with security keys. Thus critical security information would remain inaccessible to attacks even if an IoT module was physically stolen,. By encrypting critical data with keys protected by the TPM and setting a policy for when the data can be decrypted (known as “sealing”), even malware that infects the device can be prevented from accessing that data.
Conclusion
In the age of IoT and edge devices becoming essential features of homes, retail, offices, industrial complexes, automobiles, and virtually all environments, securing each interconnected element of these smart systems is necessary. As software security is inadequate to protect critical security information and keys, hardware security solutions, such as TPMs, are vital in preventing dangerous malware intrusions and information theft. To ease the use of hardware security solutions in IoT and edge devices, Infineon and Arrow deliver the Thor96 Board ARM-based SBC with the TRESOR Mezzanine Board which feature enhanced security technologies designed to offer ease of development for early development and prototyping, as well as rich features ideal for system integration.
Resources
- 1. https://www.scmagazineuk.com/dramatic-increase-iot-related-data-breaches-due-unsecured-devices/article/1584100
- 2. https://healthitsecurity.com/news/microsoft-warns-hackers-targeting-iot-devices-to-breach-networks
- 3. https://www.infineon.com/dgdl/Infineon-Why_Securing_Network__Equipment_is_Key_to_Supporting_IoT_Infrastructure-WP-v01_00-EN.pdf?fileId=5546d46265f064ff01665872e7940ce7
- 4. https://www.infineon.com/dgdl/Infineon-Securing-the-smart-and-connected-home-WP-v01_00-EN.pdf?fileId=5546d462689a790c01690e9de8df380c
- 5. https://www.infineon.com/cms/en/product/security-smart-card-solutions/optiga-embedded-security-solutions/optiga-tpm/
- 6. https://www.youtube.com/watch?v=gRatJHpIM0A
- 7. https://www.96boards.org
- 8. https://www.arrow.com/products/i.imx8-thor96/arrow-development-tools
- 9. https://www.arrow.com/products/tresor/arrow-development-tools
- 10. https://fae.technology/en/prodotti/tresor/
- 11. https://www.infineon.com/cms/en/product/security-smart-card-solutions/optiga-embedded-security-solutions/optiga-trust/optiga-trust-e-sls-32aia/
Ähnliches Produkt:
Ähnliches Produkt:
OPTIGATRUSTMEVALKITTOBO1
Infineon Technologies AG Eingebettete Systementwicklungsboards und -kits AnzeigenÄhnliches Produkt:
S2GOSECURITYOPTIGAMTOBO1
Infineon Technologies AG Eingebettete Systementwicklungsboards und -kits AnzeigenÄhnliches Produkt:
Ähnliches Produkt:
S2GOSECURITYOPTIGAXTOBO1
Infineon Technologies AG Eingebettete Systementwicklungsboards und -kits AnzeigenÄhnliches Produkt:
Ähnliches Produkt:
Ähnliches Produkt:
Ähnliches Produkt:
Ähnliches Produkt:











